- Related articles
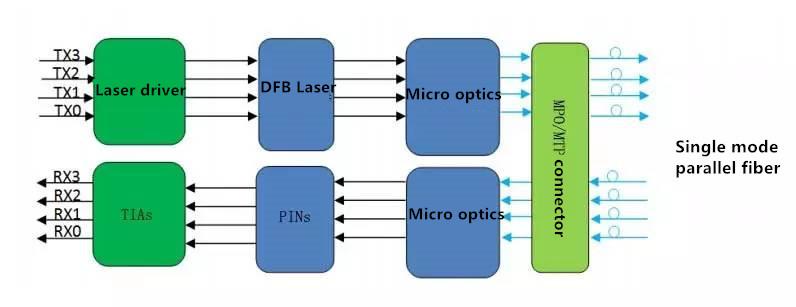
- Applicable to 10GBASE-LW Standard Optical Transceiver Models
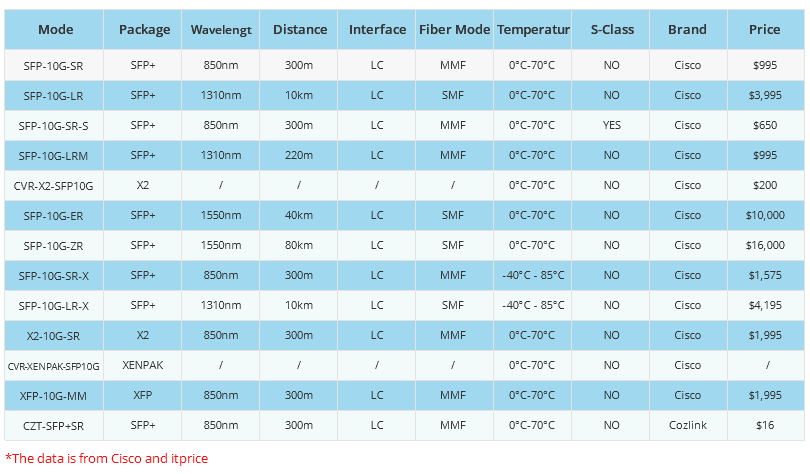
- The datasheet of Cisco SFP-10G-SR
- All Cisco SFP-10GB-LR's information (List price, Specs, Datasheet PDF, Compatibility matri
- All Cisco ONS-SC-GE-SX's information (List price, Specs, Datasheet PDF, Compatibility matr
- All Cisco CWDM-GBIC-1570's information (List price, Specs, Datasheet PDF, Compatibility ma
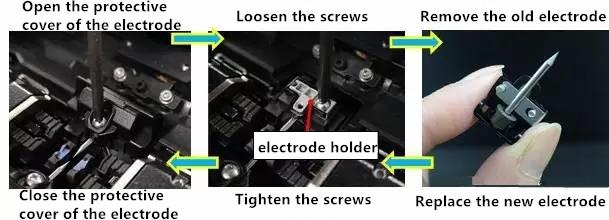
- The difference between CSFP and SFP
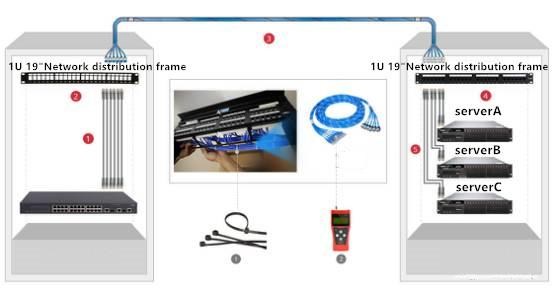
- Optimizing Virtual Infrastructures by Using Multiport Network Card
- How to Change PCI-E Speed?
- Optical Transceivers for Cisco SF300-24PP-K9-UK Switch
- Optical Transceivers for Cisco SF250-48-K9-EU Switch

Definition:
A pluggable authentication module (PAM) is a mechanism to integrate multiple low-level authentication schemes into a high-level application programming interface (API). It allows programs that rely on authentication to be written independently of the underlying authentication scheme. PAM was first proposed by Sun Microsystems in an Open Software Foundation Request for Comments (RFC) 86.0 dated October 1995. It was adopted as the authentication framework of the Common Desktop Environment. As a stand-alone open-source infrastructure, PAM first appeared in Red Hat Linux 3.0.4 in August 1996. PAM is currently supported in the AIX operating system, DragonFly BSD, FreeBSD, HP-UX, Linux, Mac OS X, NetBSD and Solaris.
What Is Pam Authentication in Linux?
Pluggable authentication modules are a common framework for authentication and security. Both of Red Hat Enterprise Linux's single sign-on methods — Kerberos and smart cards — depend on underlying PAM configuration. Programs that grant users access to a system use authentication to verify each other's identity (that is, to establish that a user is who they say they are). Historically, each program had its own way of authenticating users. In Red Hat Enterprise Linux, many programs are configured to use a centralized authentication mechanism called Pluggable Authentication Modules (PAM).
Pluggable Authentication Module (PAM) Provides:
PAM offers the following advantages:
- A common authentication scheme that can be used with a wide variety of applications
- Significant flexibility and control over authentication for both system administrators and application developers.
- A single fully-documented library which allows developers to write programs without having to create their own authentication schemes.
Conclusion:
The benefit of PAM is that it separates the details of how "authentication-related activities" are to be performed from the applications that need to carry out these activities. This makes it relatively easy to change your security policy, or to add new authentication mechanisms, simply by reconfiguring PAM. In the era before PAM, changes like that would have required source-code changes to the applications themselves. Each module performs one specific task, and a "PAM-aware" application typically uses a stack of several modules to get the job done. Figure 1 below shows the overall architecture.
Programs that grant users access to a system use authentication to verify each other's identity (that is, to establish that a user is who they say they are). Historically, each program had its own way of authenticating users. In Red Hat Enterprise Linux, many programs are configured to use a centralized authentication mechanism called Pluggable Authentication Modules (PAM). PAM uses a pluggable, modular architecture, which affords the system administrator a great deal of flexibility in setting authentication policies for the system.
Please click to check more related concepts:
| Authentication Modules |