- Related articles
- All Cisco DWDM-XFP-35.04's information (List price, Specs, Datasheet PDF, Compatibility ma
- What Is GYFTY53 Optical Fiber Cable?
- Buying guide :What is transceiver and what does it do?
- Optical Transceivers for Cisco WS-C3560E-48TD-E Switch
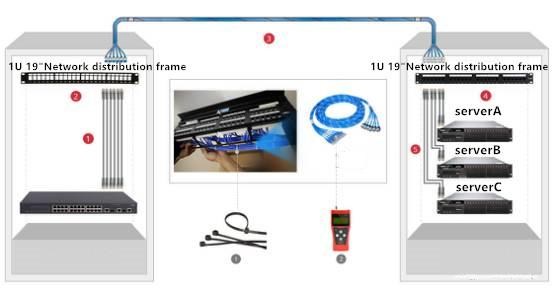
- Things you need to know about integrated network card
- All Cisco CWDM-GBIC-1550's information (List price, Specs, Datasheet PDF, Compatibility ma
- Optical Transceivers for Cisco SG200-26FP-EU Switch
- Optical Transceivers for Cisco ME-3400E-24TS-M Switch
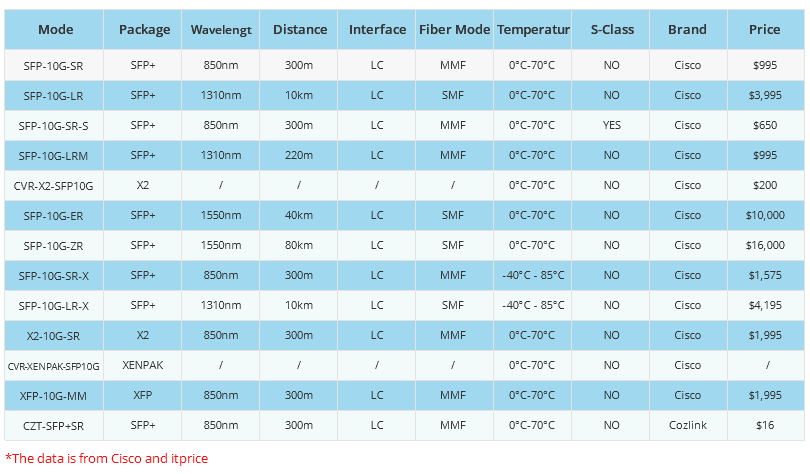
- Cisco XFP vs. SFP vs. SFP+
- All Cisco WS-G5486's information (List price, Specs, Datasheet PDF, Compatibility matrix)

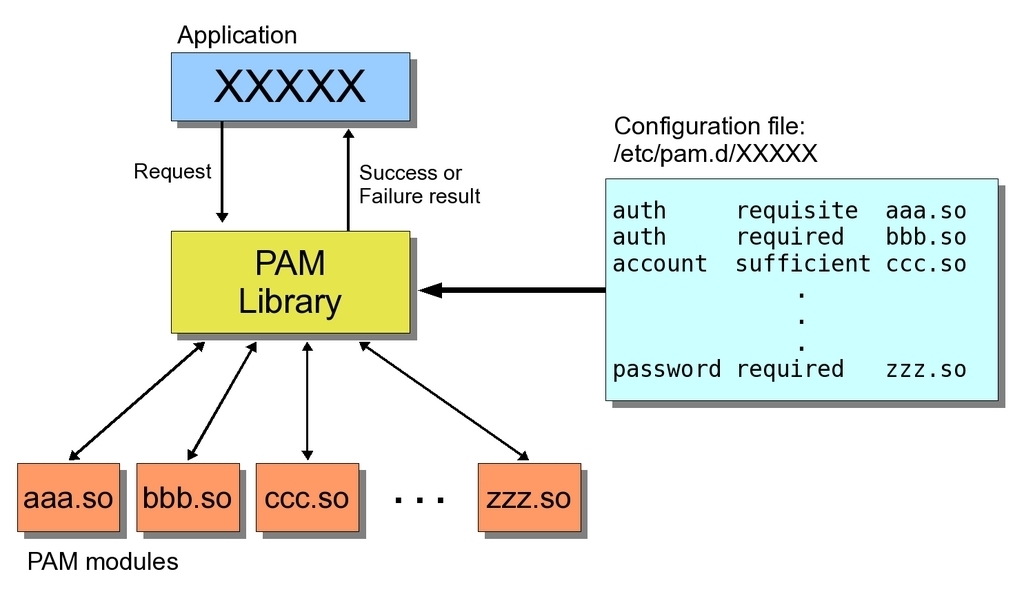
PAM Definition
PAM is pluggable authentication module. This is a mechanism to integrate multiple low-level authentication schemes into a high-level application programming interface (API). It allows programs that rely on authentication to be written independently of the underlying authentication scheme. PAM was first proposed by Sun Micro-systems in an Open Software Foundation Request for Comments (RFC) 86.0 dated October 1995. It was adopted as the authentication framework of the Common Desktop Environment. As a stand-alone open-source infrastructure, PAM first appeared in Red Hat Linux 3.0.4 in August 1996. PAM is currently supported in the AIX operating system, DragonFly BSD, FreeBSD, HP-UX, Linux, Mac OS X, NetBSD and Solaris.
Since no central standard of PAM behavior exists, there was a later attempt to standardize PAM as part of the X/Open UNIX standardization process, resulting in the X/Open Single Sign-on (XSSO) standard. This standard was not ratified, but the standard draft has served as a reference point for later PAM implementations.
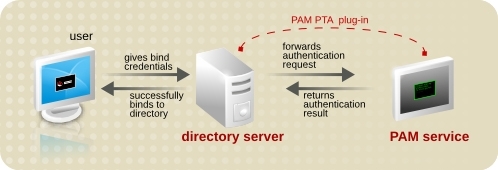
Since most PAM implementations do not interface with remote clients themselves, PAM on its own cannot implement Kerberos, the most common type of SSO used in Unix environments. This led to SSO's incorporation as the "primary authentication" portion of the would-be XSSO standard and the advent of technologies such as SPNEGO and SASL. This lack of functionality is also the reason SSH does its own authentication mechanism negotiation.
In most PAM implementations, pam_krb5 only fetches Ticket Granting Tickets, which involves prompting the user for credentials and are only used for initial login in an SSO environment. To fetch a service ticket for a particular application, and not prompt the user to enter credentials again, that application must be specifically coded to support Kerberos, as pam_krb5 cannot itself get service tickets, although there are versions of PAM-KRB5 that are attempting to work around the issue.
Cozlink could find for you the different ways to integrate yours PAM modules in your system. They offer high technological innovative decisions for your needs at the best price. So you could take a look at their entire portfolio of products and if you have any questions do not hesitate to contact us.
Please click to check more related concepts:
| Framework | Authentication module |