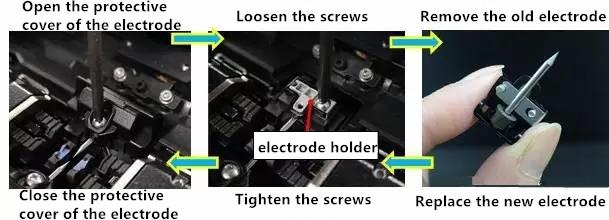
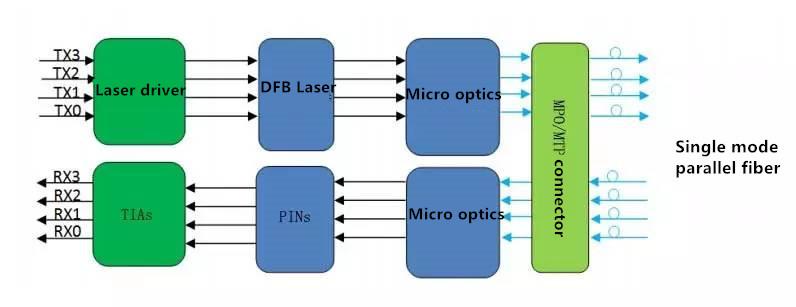
- Related articles
- Optical Transceivers for Cisco WS-C2960+48TC-L Switch
- All Cisco DWDM-XFP-54.94's information (List price, Specs, Datasheet PDF, Compatibility ma
- All Cisco ONS-SI-155-L1's information (List price, Specs, Datasheet PDF, Compatibility mat
- Optical Transceivers for Cisco SRW2048-K9-EU Switch
- How to Check Whether Network Card Is Working or Not?
- Name Brands vs Third-Party Transceivers: Which Do You Prefer?
- All Cisco DS-CWDM4G1550's information (List price, Specs, Datasheet PDF, Compatibility mat
- Optical Transceivers for Cisco WS-C3560V2-48TS-S Switch
- All Cisco CWDM-SFP-1610's information (List price, Specs, Datasheet PDF, Compatibility mat
- Optical Transceivers for Cisco SM-D-ES3G-48-P= Switch
Recommend tag

What is Linux PAM module?
2016-07-14
Definition:
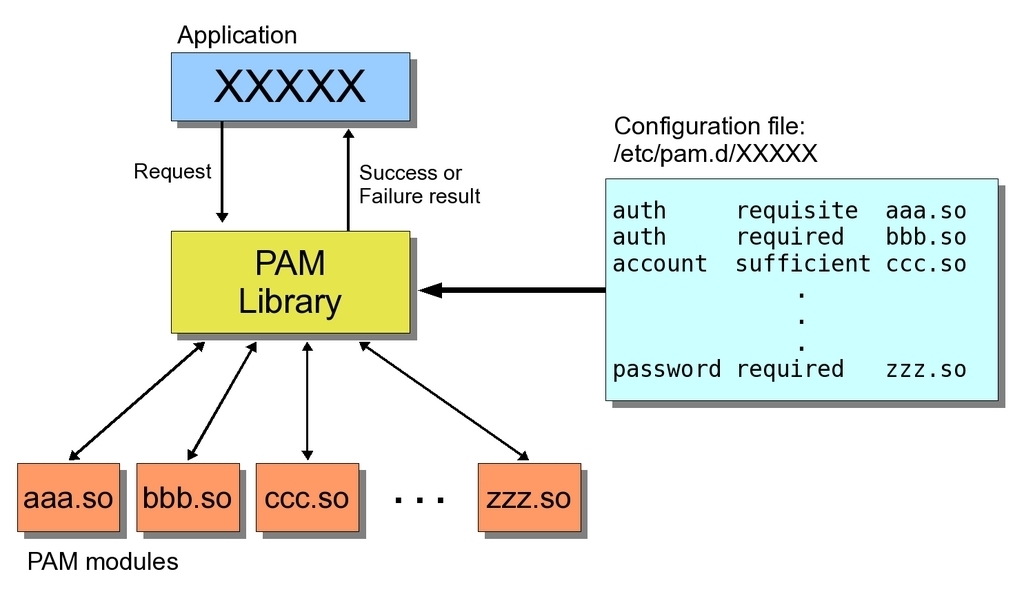
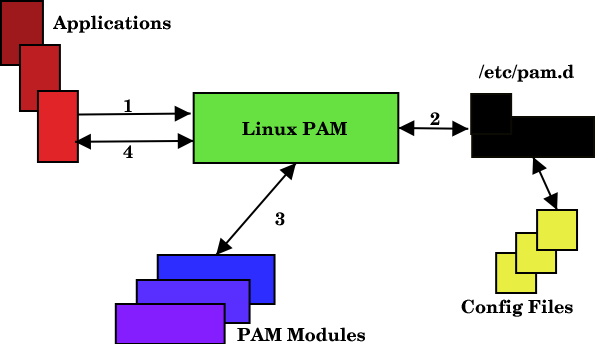
Linux Pluggable Authentication Modules (PAM) provide dynamic authentication support for applications and services in a Linux or GNU/kFreeBSD system. Linux PAM module is evolved from the Unix Pluggable Authentication Modules architecture. Linux PAM module uses a pluggable, modular architecture, which affords the system administrator a great deal of flexibility in setting authentication policies for the system.
Function:
Linux PAM module separates the tasks of authentication into four independent management groups:
- Account modules check that the specified account is a valid authentication target under current conditions. This may include conditions like account expiration, time of day, and that the user has access to the requested service.
- Authentication modules verify the user's identity, for example by requesting and checking a password or other secret. They may also pass authentication information on to other systems like a keyring.
- Password modules are responsible for updating passwords, and are generally coupled to modules employed in the authentication step. They may also be used to enforce strong passwords.
- Session modules define actions that are performed at the beginning and end of sessions. A session starts after the user has successfully authenticated.
Purpose:
It is the purpose of the Linux PAM module to separate the development of privilege granting software from the development of secure and appropriate authentication schemes. This is accomplished by providing a library of functions that an application may use to request that a user be authenticated." With Linux PAM module, it doesn't matter whether your password is stored in. When a program needs to authenticate a user, Linux PAM module provides a library containing the functions for the proper authentication scheme. Because this library is loaded dynamically, changing authentication schemes can be done by simply editing a configuration file.
Strengths:
Flexibility is one of Linux PAM module greatest strengths. PAM can be configured to deny certain programs the right to authenticate users, to only allow certain users to be authenticated, to warn when certain programs attempt to authenticate, or even to deprive all users of login privileges. Linux PAM module design gives you complete control over how users are authenticated.
Please click to check more related concepts:
| Framework | Authentication module |

TECHNICAL SUPPORT
Get solutions or consultation from the technical team.